EN - eLearning - EC-Council Computer Hacking Forensic Investigator (CHFI) v11
Exam voucher: Included (valid for 12 months) + 2nd try |
Course material e-book: Included |
Video training: Included for eLearning courses only |
Download Brochure
If you want to learn more about the training, check out the official training brochure!
What you'll get
- One (1) Year Access to the e-courseware.
- Six (6) months access to EC-Council's official online lab environment.
- Certification or Exam voucher valid for a period of one (1) year.
- Certification and examination fees are included in the price of the training course.
- Expert instructor-led training modules with streaming video presentations and learning supplements for an all-inclusive training program that provides the benefits of classroom training at your own pace with a validity of one (1) year.
- 20% reduction on the first year subscription for our all-in-one ISMS/GRC management solution
Official ECC-Reseller-Certificate
As per Statista, In 2022, phishing topped cybercrimes reported to the US Internet Crime Complaint Center, affecting about 300k individuals, with nearly 59k personal data breaches reported.
In 2022, investment fraud led to the highest financial losses for individuals in the US, totaling over $3 billion. Business email compromise (BEC) followed with reported losses of around $2.7 billion, while victims of tech support fraud reported losses of $806 million.
Dark web statistics show that in 2020, cyber criminals added over 22 billion new records to the dark web.
The global average cost of a data breach in 2023 was $4.45 million, a 15% increase over three years (IBM).
According to the source, approximately 52 percent of respondents in the United States stated that their company had in place a dark web threat intelligence policy in 2022.
Over 90% of all crime is recognized as having a digital element, highlighting the movement of present-day policing towards having technology at its core.
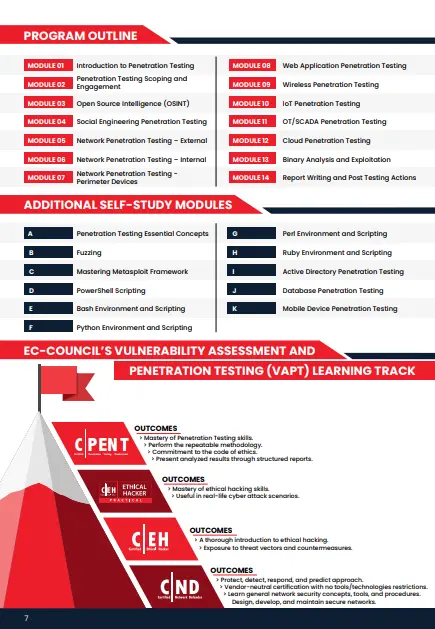
Why Choose CHFI
EC-Council’s C|HFI program prepares cybersecurity professionals with the knowledge and skills to perform effective digital forensics investigations and bring their organization into a state of forensic readiness. Establishing the forensics process, lab, evidence handling procedures, and investigation techniques are required to validate/triage incidents and point the incident response teams in the right direction. Forensic readiness is crucial as it can differentiate between a minor incident and a major cyber-attack that brings a company to its knees.
This intense hands-on digital forensics program immerses students in over 68 forensic labs, working on crafted evidence files utilizing the tools of the world’s top digital forensics professionals. Students will go beyond traditional hardware and memory forensics, covering current topics in cloud forensics, mobile and IoT, and investigating web application attacks and malware forensics. The C|HFI presents a methodological approach to computer forensics, including searching and seizing, chain-of-custody, acquisition, preservation, analysis, and reporting of digital evidence.
Students learn various forensic investigation techniques and standard forensic tools. As they learn how to acquire and manage evidence through various operating environments, students also learn the chain of custody and legal procedures required to preserve evidence and ensure it is admissible in court, enabling the eventual prosecution of cyber criminals and containing liability on the victim organization.
The program provides credible professional knowledge with globally recognized certification required for a successful digital forensics and DFIR career, thus increasing your employability.
Who should take this course?
- Digital Forensics Analyst
- Security Engineer – Forensics
- Cryptanalyst
- Cloud Security Analyst
- Computer Forensic Analyst/Practitioner
- Malware Analyst
- Cybersecurity/Defense Forensics Analyst
- Cryptographer
- Forensics SME
- Cybercrime Investigator
- Mobile Forensic Analyst/Expert
- Disaster Recovery Expert
- Forensic Accountant
- Computer Crime Investigator
- Mobile Exploitation Analyst
- Intelligence Technology Analyst
- IT Security Forensic Analyst
- Cyber Defense Forensics Analyst
- Information Systems Security Professional
- Cybersecurity Incident Response and Attack Analyst
Covering domains of digital forensics
Pages of the student manual
Pages of lab manual covering lab scenarios and instructions
Hands-on lab
Digital forensic tools covered
Of crafted evidence files for investigation purposes
Key Features
Course Modules
Module | Description |
| Computer Forensics in Today's World | Computer forensics fundamentals, different types of cybercrimes and their investigation procedures, and regulations and standards that influence computer forensics investigation. |
Computer Forensics Investigation Process | Various phases involved in the computer forensics investigation process. |
Understanding Hard Disks and File Systems | Different types of disk drives and their characteristics, booting process and file systems in Windows, Linux, and Mac operating systems, file system examination tools, RAID and NAS/SAN storage systems, various encoding standards, and file format analysis. |
Data Acquisition and Duplication | Data acquisition fundamentals and methodology, eDiscovery, and how to prepare image files for forensics examination. |
Defeating Anti-Forensics Techniques | Various anti-forensics techniques used by attackers, different ways to detect them and related tools, and countermeasures. |
Windows Forensics | Volatile and non-volatile data acquisition in Windows-based operating systems, Windows memory and registry analysis, electron application analysis, Web browser forensics, and examination of Windows files, ShellBags, LNK files, and Jump Lists, and Windows event logs. |
Linux and Mac Forensics | Volatile and non-volatile data acquisition and memory forensics in Linux and Mac operating systems. |
Network Forensics | Network forensics fundamentals, event correlation concepts, Indicators of Compromise (IOCs) and ways to identify them from network logs, techniques and tools related to network traffic investigation, incident detection and examination, and wireless attack detection and investigation. |
Malware Forensics | Malware forensics concepts, static and dynamic malware analysis, system and network behavior analysis, and ransomware analysis. |
Investigating Web Attacks | Web application forensics and challenges, web application threats and attacks, web application logs (IIS logs, Apache web server logs, etc.), and how to detect and investigate various web application attacks. |
Dark Web Forensics | Tor browser working methodology and steps involved in the Tor browser forensics process. |
Cloud Forensics | Cloud computing concepts, cloud forensics, and challenges, fundamentals of AWS, Microsoft Azure, and Google Cloud and their investigation processes. |
Email and Social Media Forensics | Components in email communication, steps involved in email crime investigation, and social media forensics. |
Mobile Forensics | Architectural layers and boot processes of Android and iOS devices, mobile forensics process, various cellular networks, SIM file system, and logical and physical acquisition of Android and iOS devices. |
IoT Forensics | Different types of IoT threats, security problems, vulnerabilities and attack surfaces areas, and IoT forensics process and challenges. |
Achieving the CHFI Certification Credential
CHFI (ANSI)
Exam Title: Computer Hacking Forensics Investigator (ANSI)
Exam Code: 312-49 (ECC Exam Portal)
Number of questions: 150
Durations: 4 hours of theory and 6 Hours of practice
Availability: ECC EXAM*
Passing score: 60-85%
- Local proctor for Private and in-person courses.
- Live remote proctor for online ECC Exam option.
Passing score: Please refer to https://cert.eccouncil.org/faq.html

Testimonial
Ask any question about our products
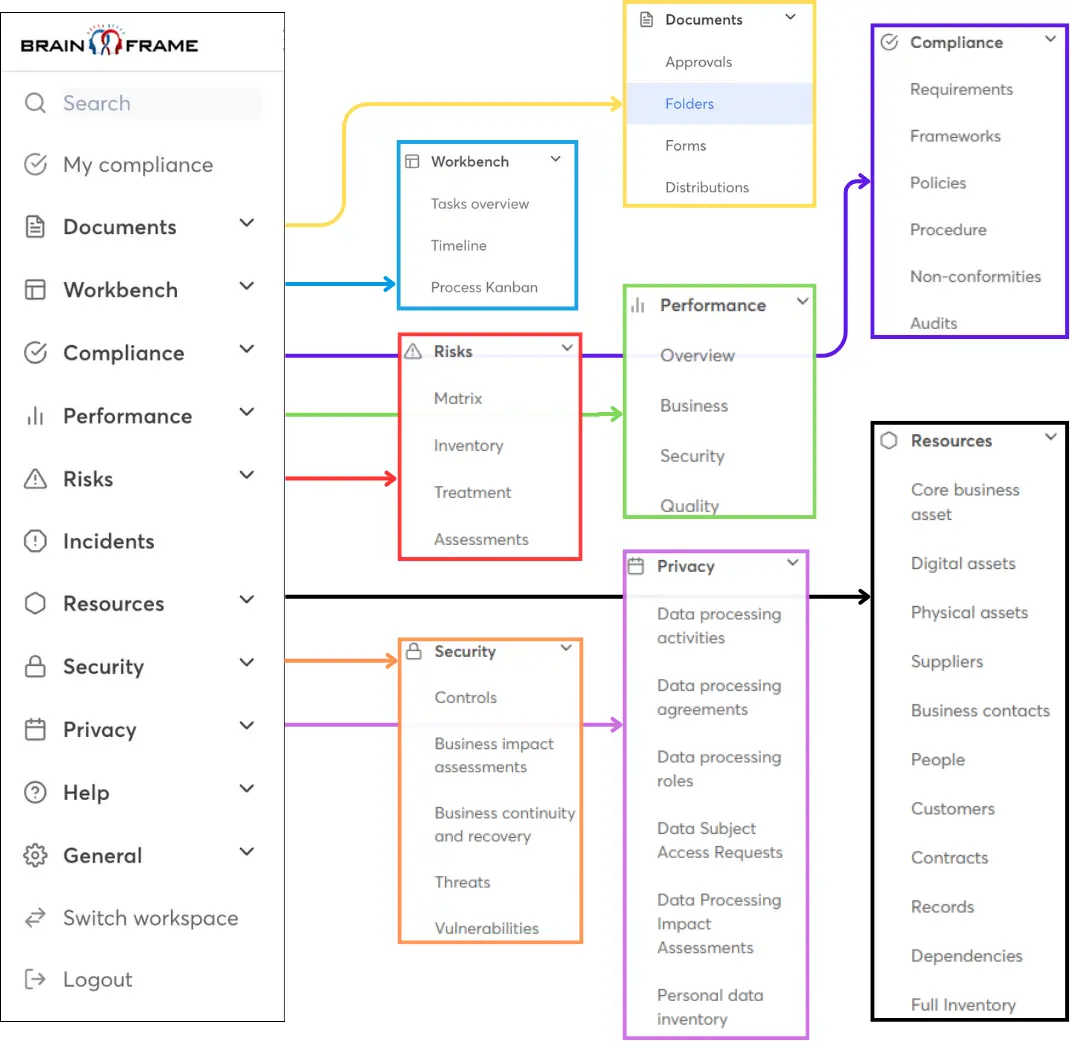
Streamline your GRC work using our all-in-one management solution and get access to our network of local specialists
Start your free account
%20v11?unique=aca23db)