EN - eLearning - EC-Council Certified Penetration Testing Professional (CPENT)
Master best in-class penetration testing skills to safeguard enterprises against advanced cyber-attacks
Examenbon: Inbegrepen (geldig voor 12 maanden) + 2e poging |
Cursusmateriaal e-boek: Inbegrepen |
Video materiaal: Enkel inbegrepen voor eLearning cursussen |
Download Brochure
If you want to learn more about the training, check out the official training brochure!
What you'll get
- One (1) Year Access to the e-courseware.
- Six (6) months access to EC-Council's official online lab environment.
- Certification or Exam voucher valid for a period of one (1) year.
- Certification and examination fees are included in the price of the training course.
- Expert instructor-led training modules with streaming video presentations and learning supplements for an all-inclusive training program that provides the benefits of classroom training at your own pace with a validity of one (1) year.
- + 20% reduction on the first year subscription for our all-in-one ISMS/GRC management solution
Why Choose CPENT
A rigorous Penetration Testing program that, unlike contemporary Penetration Testing courses, teaches you how to perform an effective Penetration test across filtered networks.
C|PENT is a multidisciplinary course with extensive hands-on training in a wide range of crucial skills, including advanced Windows attacks, Internet of Things (IoT) and Operational Technology (OT) systems, filtered network bypass techniques, exploit writing, single and double pivoting, advanced privilege escalation, and binary exploitation. In summary, there is no program of its kind in the world!
The CPENT Range
The C|PENT range, which is where our Penetration Testers gain real-world skills, is designed to provide challenges across every level of the attack spectrum. Additionally, the range contains multiple layers of network segmentation, and once access is gained in one segment, the latest pivoting techniques are required to reach the next segment.
Many of the challenges will require outside-the-box thinking and customization of scripts and exploits to get into the innermost segments of the network. The key to being a highly skilled Penetration Tester is to go up against various targets that are configured in a variety of ways.
The C|PENT consists of entire network segments that replicate an enterprise network — this is not a computer game simulation; this is an accurate representation of an enterprise network that will present the latest challenges to the Penetration Tester.
Since the targets and technology continue to change, the C|PENT is dynamic, and machines and defenses will be added as they are observed in the wild. Finally, the targets and segments are progressive in nature. Once you get into one machine and or segment, the next one will challenge you even more.
Who should take this course?
- Ethical Hackers
- Application Security Analyst
- Cybersecurity Forensic Analyst
- Cybersecurity Assurance Engineer
- Penetration Testers
- Security Operations Center (SOC) Analyst
- Cyberthreat Analyst
- Technical Operations Network Engineer
- Network Server Administrators
- Information Security Engineer
- Firewall Administrators
- Network Security Penetration Tester
- System Administrators and Risk Assessment Professionals
- Cloud Security
- Security Testers
- Network Security Engineer
- Analyst Information Security Consultant
- Information Security Architect
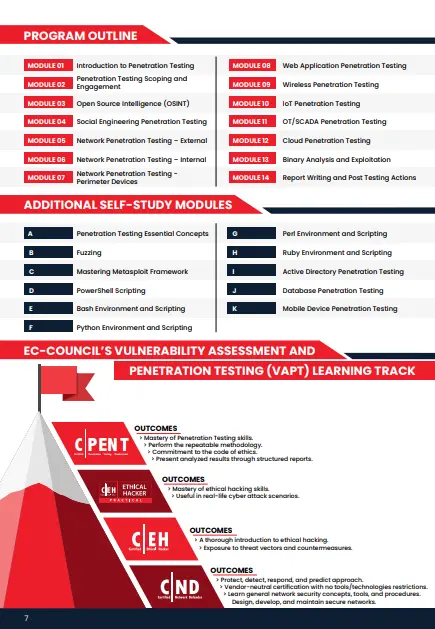
Course Modules
| Skills learned with CPENT | Description |
|---|---|
| Advanced Windows Attacks | This zone contains a complete forest that you first have to gain access to, using PowerShell bypass techniques and advanced methods like executing Silver and Gold Ticket attacks and Kerberoasting. Machines are configured with defenses in place to challenge your skills. |
| Attacking IoT Systems | Locate IoT devices, gain access to their network, identify firmware, extract it, and reverse engineer it. The focus is on understanding IoT device vulnerabilities and exploiting them. |
| Writing Exploits: Advanced Binary Exploitation | Find flawed binaries, reverse engineer them, and write exploits to take control of program execution. Challenges include handling 32-bit and 64-bit code with protections like non-executable stacks. Debugging and advanced techniques like egg hunting are required. |
| Bypassing a Filtered Network | Identify the segmentation architecture, exploit filtering techniques, and compromise web applications. The goal is to extract the required data to achieve points. |
| Pentesting Operational Technology (OT) | Penetrate ICS/SCADA networks from the IT side, access the OT network, identify PLCs, and modify data to impact the network. The focus includes intercepting Modbus communication protocols. |
| Access Hidden Networks with Pivoting | Identify network filtering rules and penetrate the direct network. Utilize single pivoting methods to move into hidden networks, bypassing filters. |
| Double Pivoting | Go beyond single pivoting by manually setting up double pivoting techniques to access hidden networks. Tools cannot automate this process. |
| Privilege Escalation | Learn the latest methods to reverse engineer code, control execution, and escalate privileges from limited shells to root/admin access. |
| Evading Defense Mechanisms | Explore methods to weaponize exploits to bypass defensive mechanisms like firewalls and intrusion detection systems. |
| Attack Automation with Scripts | Use scripting languages like Ruby, Python, PowerShell, Perl, and Bash for advanced penetration testing techniques, including fuzzing and automation. |
| Build Your Armory: Weaponize Your Exploits | Carry your own tools and build your armory with custom coding expertise to tackle challenges like a real-world penetration tester. |
| Write Professional Reports | Understand how to mitigate risks, validate findings, and produce impactful penetration testing reports for clients. |

Achieving the CEH Certification Credential
Exam Title: Certified Penetration Testing Professional
Exam Code: 412-80
Number of questions: 150
Durations: 2 x 12 Hours or 1 x 24 hours
Availability: Online
Passing score: 70-90%
- Local proctor for Private and in-person courses.
- Live remote proctor for online ECC Exam option.
Candidates who score more than 90% will establish themselves as the Penetration
Testing Masters and attain the prestigious LPT (Master) credential!

Testimonial
Stel eender welke vraag over onze producten
Stroomlijn uw GRC-werk met onze alles-in-één managementoplossing en krijg toegang tot ons netwerk van lokale specialisten
Start je gratis account
?unique=f3e9014)